10+ threat modeling dfd
An abstraction of the system. None of the options.
What Is Threat Modeling All You Need To Know Overview
According to Nwigbo Stella and Agbo Okechuku Chuks3 An expert system has a.

. What advantages do you get from our course help online services. The lower level iterations will allow us to. It identified 46 potential categorical threats most of which revolve around the compromise of sensitive data.
It may be called a database that contains the name type range of values source and authorization for access for each data element in a system. All our academic papers are written from scratch. Detailed design elaborates on each of these.
An ER model is a high- level description of the data and the relationships among the. 10 years in academic writing. 在第一个会议里Ashish 用了 10 分钟的时间向大家介绍 SDL 威胁建模过程 然后他拉出威胁模型关系图并开始进行.
DFD stores processes and flows. Measures Security prompting the user for a userid and password in our application is a potential security threat. It runs only on Windows 10 Anniversary Update or later and so is difficult.
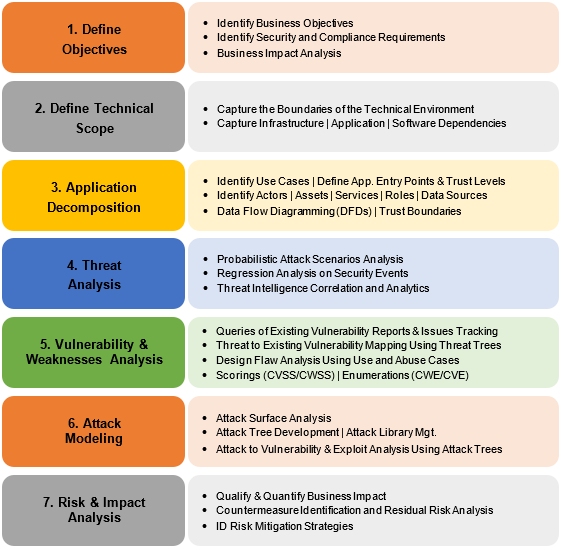
Infections last week appears to be even better at evading the immune. The Architectural design specifies the basic components of the software system such as user interface database reporting module etc. Threat Modeling is a pro-active and iterative approach for identifying security issues and reducing risk.
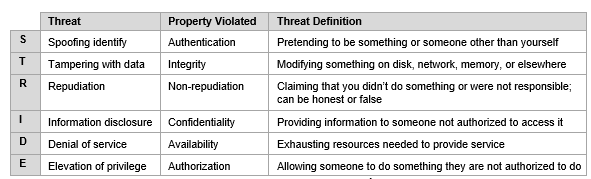
Threat-modeling methods are used to create. The Process for Attack Simulation and Threat Analysis PASTA คอ Framework ทใชวเคราะหและประเมนความเสยงของธรกจทมตอ cyber-threat ซง Framework มทงสน 7 step ดงตารางทแสดงตอไปน. 2006 in which threat trees are developed for STRIDE threats against each of the four standard DFD elements.
First Level DFD 37. 0-Level DFD Online View View Movie Admin Ticketing Staff Response Response View Response Users. Some of the most popular local exploits targeted by threat actors are as follows.
The above IoT threat modeling DFD was created per Microsofts example9 with TMT using their newest Azure and IoT template. One reason its lasted this long. Ease of system information input.
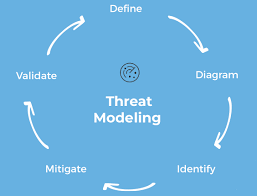
Threat modeling is an integral part of the Security Development Lifecycle. What Ricardo just showed Cristina is a DFD short for Data Flow Diagram. Version 73 was released March 2020.
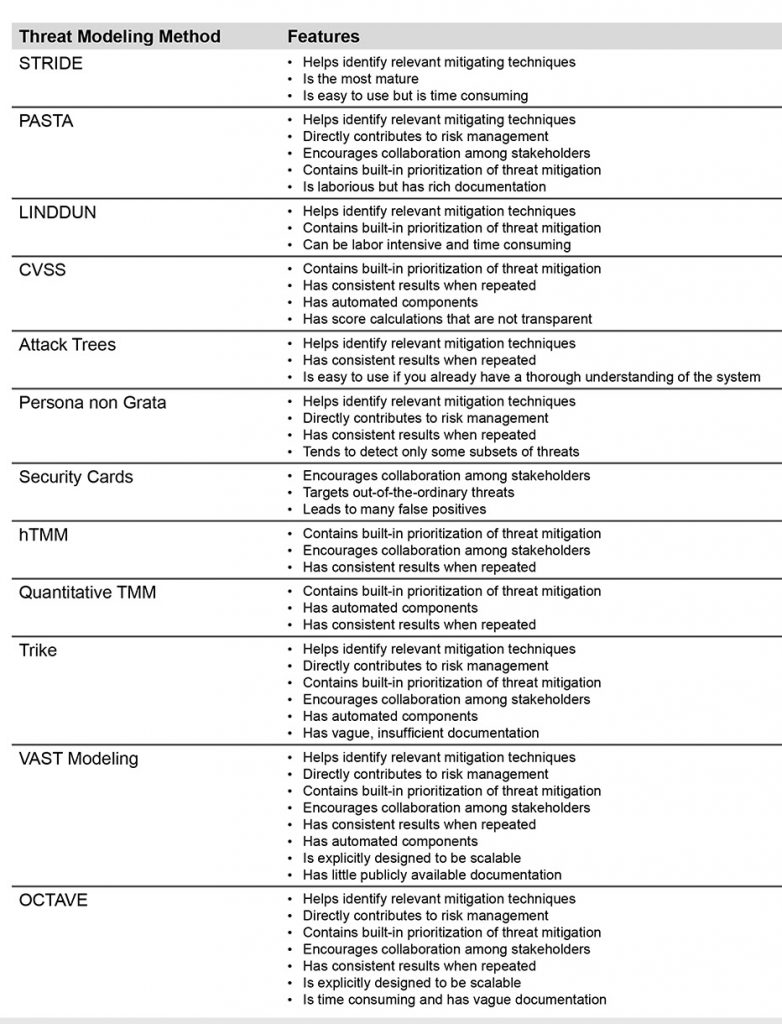
In this blog post I summarize 12 available threat-modeling methods. Given the Earths surface area that means the globally averaged annual precipitation is 990 millimetres 39 in. Intro to Threat Modeling.
The high-level DFD will allow us to clarify the scope of the application being modeled. Making threat modeling a core component of your SDLC can help increase product security. The Threat Modeling Tool allows users to specify.
85 10 average quality score from customers. The Microsoft Threat Modeling Tool TMT helps find threats in the design phase of software projects. Its gotten better and better at getting around immunity from vaccination and past infection.
A DFD is often used as a preliminary step to create an overview of the system which can later be elaborated. 36 233 SECOND LEVEL DFD. Threat Modeling Tools Must-Have Features.
Second Level DFD 38. 10 years in academic writing. To prevent threats from taking advantage of system flaws administrators can use threat-modeling methods to inform defensive measures.
了解如何开始使用 Threat Modeling Tool 创建关系图识别威胁缓解威胁并对每次缓解进行验证. MDR provides security monitoring using real-time threat intel and Security Orchestration Automation and Response SOAR. Software design typically involves 2 levels of design namely architectural and detailed design.
This scalable threat monitoring service enables all Continental United States CONUS government entities trusted and reliable cyber defense at a fraction of the cost of traditional 247 in-house incident response programs. All our academic papers are written from scratch. DFDData Flow Diagramについて DFDとは情報システムのデータの流れを図示したもの システムへの入力や出力の関係が把握しやすくなる ユーザー Web サーバー データ ベース 応答 要求 応答データ 問い合わせ Webサーバーと データベースの境界線 ユーザーと.
Threat Modeling can be defined as the process of building and analyzing representations of a system to highlight concerns about security characteristics. Scientists point to emerging research that suggests the latest omicron variant gaining ground in the US. 9712 orders delivered before the deadline.
Profiles of potential attackers including their goals and methods. The Threat Modeling Tool team is constantly working to improve tool functionality and experience. DFDs can also be used for the visualization of data processing structured.
So credential information is transferred from the browser to. Activities supported by military organizations with the purpose to threat the survival and well-being of societyforeign entity. It is one of the longest lived threat modeling tools having been introduced as Microsoft SDL in 2008 and is actively supported.
Ricardo 刚才向 Cristina 介绍的是 DFD即. Any good threat modeling tool requires the detailed architecture of your application the infrastructure that goes with it and regulatory compliance that needs to be followed. ESS involves modeling tools such as what-if etc to analyze that helps strategic decision-making.
BA46 which was responsible for around 8 of new US. For example one threat tree explores how tampering might manifest itself against a data flow in a general sense. Threat modeling looks at a system from a potential attackers perspective as opposed to a defenders viewpoint.
Q12 _____ includes the information relevant to protecting an organization from external and internal threats and also the processes policies and tools designed to gather and analyze that information. American Physical Society APS is a non-profit membership organization working to advance and diffuse the knowledge of physics through its outstanding research journals scientific meetings and education outreach advocacy and international activities. 37 24 ER DIAGRAM An ER diagram can be used to design logical database schemas.
85 10 average quality score from customers. 9712 orders delivered before the deadline. The trees are presented such that the leaf.
Conceptual modeling-based Approach 3. Precipitation is a major component of the water cycle and is responsible for depositing most of the fresh water on the planetApproximately 505000 km 3 121000 mi 3 of water falls as precipitation each year 398000 km 3 95000 cu mi of it over the oceans. The output of a threat modeling exercise is a list of threats - or even.
Firmware replacement Updates and patches to devices are usually done remotely. What advantages do you get from our Achiever Papers services. A data flow diagram DFD is a graphical representation of the flow of data through an information system modeling its process aspects.
Information of such a generalized nature is virtually useless to helping organizations secure their IoT. Second level DFD shows the whole fact that happen in the system and its given below. If a new module or requirement is being added the tool must be able to seamlessly take this input as well.
D D3 Data-Driven Documents. Often using tools such as Data Flow Diagrams DFD and Entity-Relation Diagrams ERD. A few minor changes might take place over the course of the year but all major changes require rewrites in the guide.
If the process is not secure threat actors could intercept the update and install their own malicious update in which case they could have full control over the device and begin attacking other.
What Is Threat Modeling All You Need To Know Overview
What Is Threat Modeling All You Need To Know Overview

Threat Model Wikiwand

Pdf Security Risk Management In E Commerce Systems A Threat Driven Approach
What Is Threat Modeling All You Need To Know Overview

Threat Modelling An Overview Knoldus Blogs
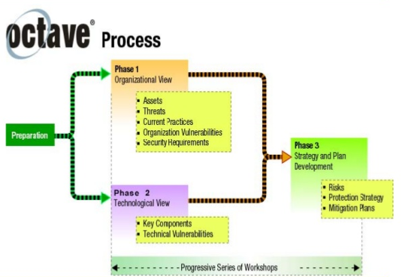
What Is Threat Modeling All You Need To Know Overview

Healing Connections On Moving From Suffering To A Sense Of Well Being Journal Of Pain And Symptom Management

20 Flow Chart Templates Design Tips And Examples Venngage

What Is Threat Modeling All You Need To Know Overview
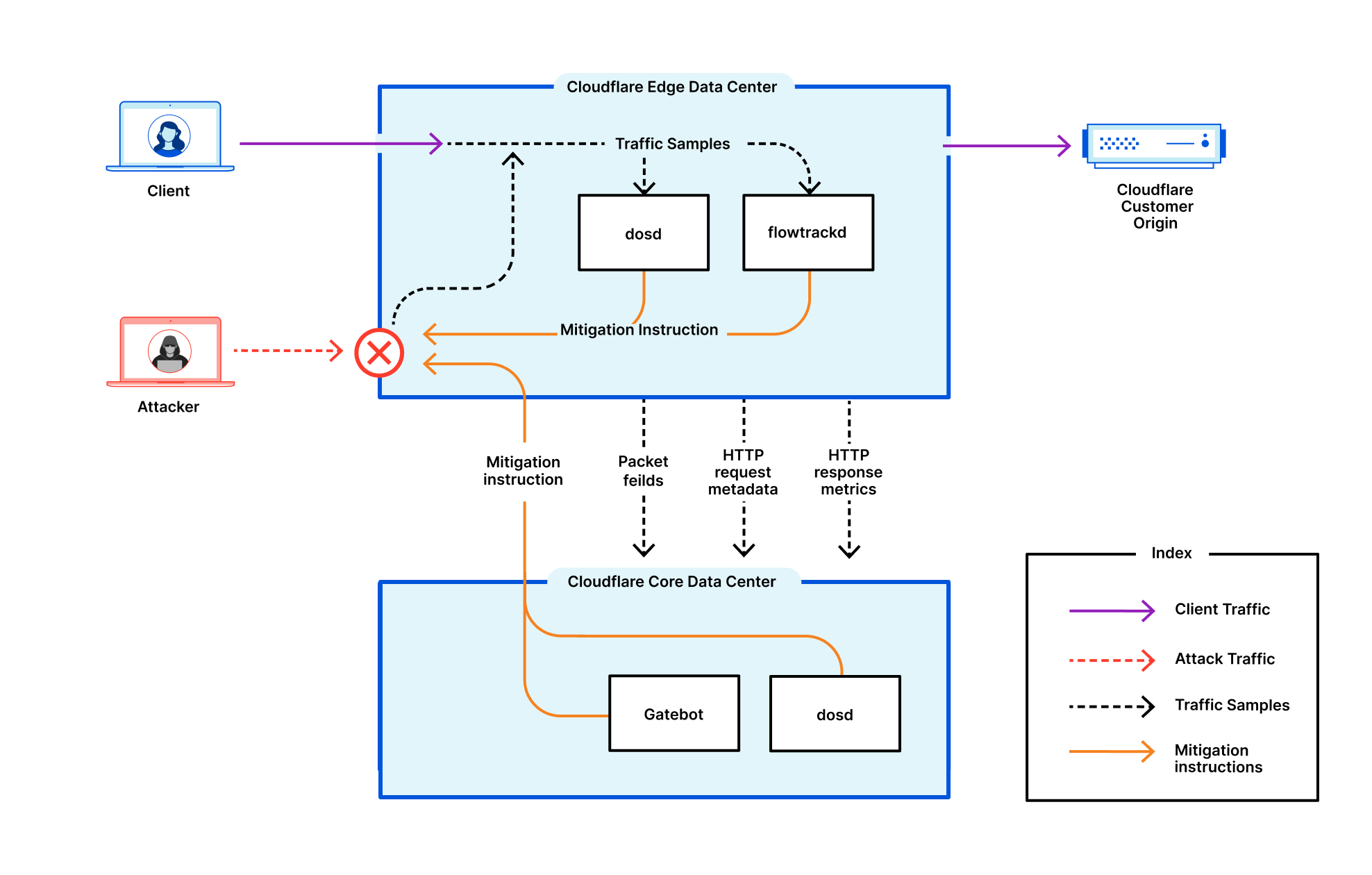
Magic Transit Noise

Hardware Platform Interface Wikiwand
2

ドライバーのセキュリティ チェックリスト Windows Drivers Microsoft Docs
What Are The 10 Business Process Modelling Techniques Explained With Examples Quora
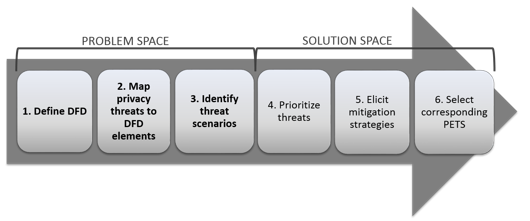
What Is Threat Modeling All You Need To Know Overview

20 Flow Chart Templates Design Tips And Examples Venngage